Users
Manage user roles, permissions, and statuses to ensure secure access and efficient operation within your organization.
Overview
The Users tab allows you to manage user accounts within your organization, including creating new users, assigning roles, and managing user statuses. The tab provides a list view of all users, displaying their name, email, status, and assigned role.
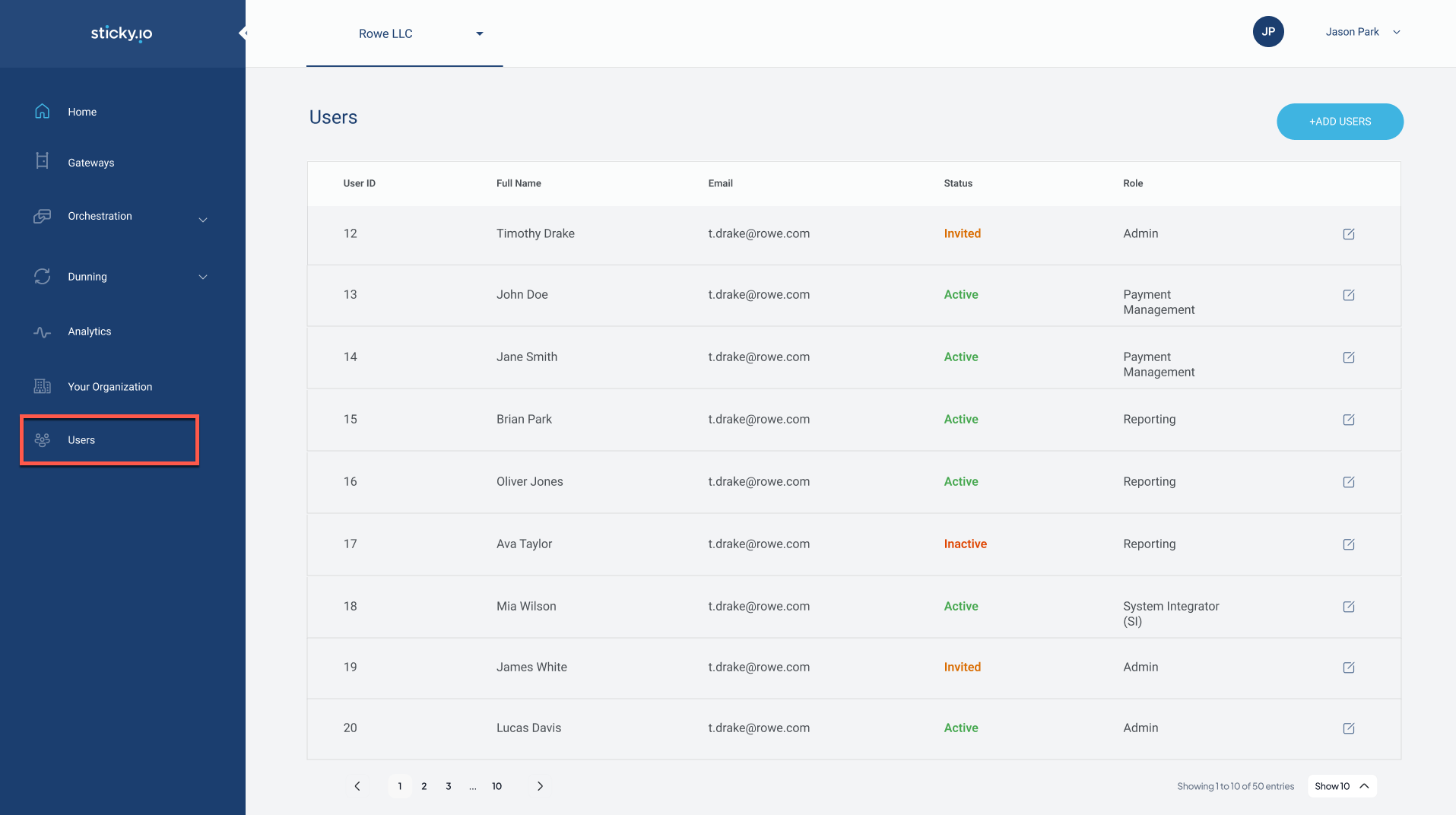
User Statuses
Each user can have one of the following statuses:
▶️ Active: The user is currently active and has access to the system.
▶️ Inactive: The user is not currently active and does not have access to the system. Inactive users can be reactivated by an admin.
▶️ Invited: The user has been invited to join the organization but has not yet accepted the invitation.
Instead of deleting users, they can be marked as inactive. This ensures that historical data and associations remain intact, allowing for accurate tracking and maintaining data integrity.
User Roles
Each user can be assigned one or more roles that define their permissions within the system. Roles determine what actions a user can perform across different modules, such as managing transactions, configuring recovery profiles, and accessing analytics. Some key roles include:
▶️ Owner: The owner of the organization who has full access to all modules and settings.
▶️ Admin: Capable of accessing, creating, and updating all content.
▶️ System Integrator (SI): Primarily responsible for technical integrations and managing API-related tasks.
▶️ Payment Management: Focused on handling payment processes and customer support tasks.
▶️ Reporting: Has access to view analytics and generate reports.
Each role has specific permissions for creating, reading, updating, or deleting data within different sections of the platform. Refer to the provided roles and permissions table for a detailed breakdown.
Add/Manage Users
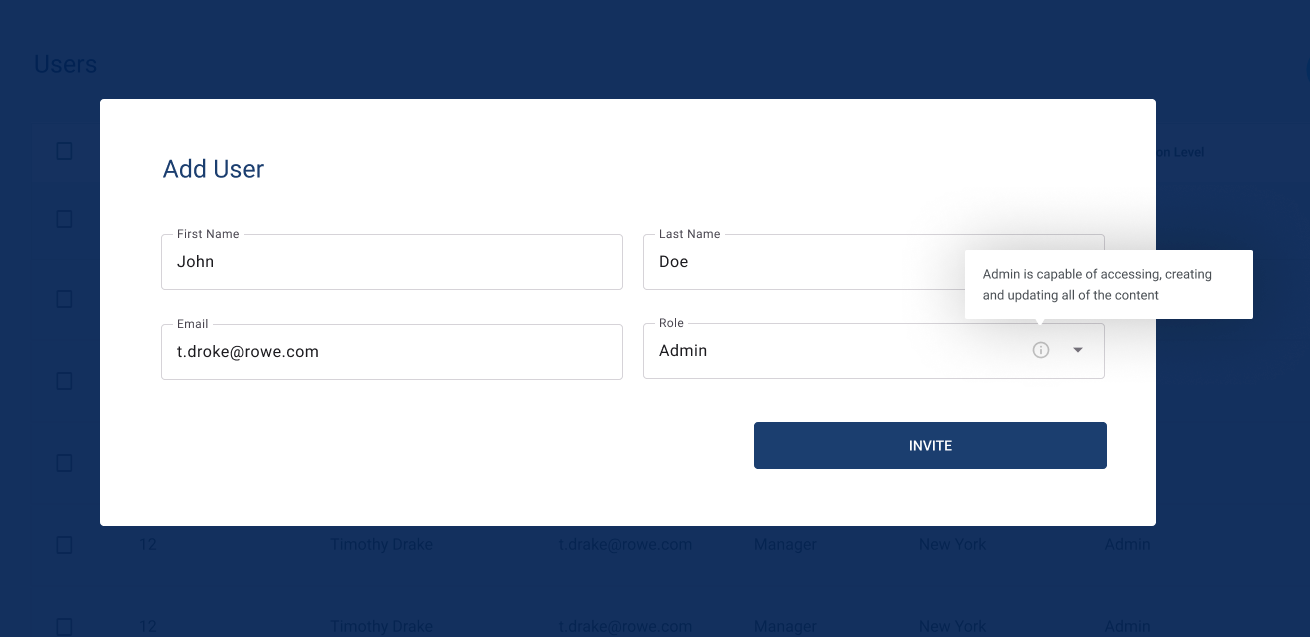
Admins or Owners can invite users to the system by sending an invitation to their provided email address.
The invitation remains pending until the user accepts it. If needed, the invitation can be canceled as long as it has not been accepted. Once a user accepts the invitation, they will be added to the system.
If necessary, the user can later be deactivated instead of deleted, preserving historical data and maintaining system integrity.
Updated 5 months ago